Technical Design Document: AuthSpoke MCP Integrated Agent IAM
1. Overview
This document describes how to integrate AuthSpoke's Agent Identity and Access Management (IAM) SDK (the AgentSpoke SDK) with a Mission Critical Processing (MCP) environment, to secure and orchestrate AI agents communicating with various applications. The design supports zero-trust principles, role-based access, and secure agent lifecycle operations, while integrating with existing MCP authorization and policy protocols.
2. Problem Statement
Organizations running MCP servers typically manage mission-critical systems with strict authentication and authorization boundaries. Introducing AI agents for data processing, predictions, or orchestration adds risk: these agents must be trusted, lifecycle-managed, and audited to avoid compromising security. An IAM layer for AI agents is essential to protect critical assets from unauthorized or uncontrolled AI behavior.
3. Architecture
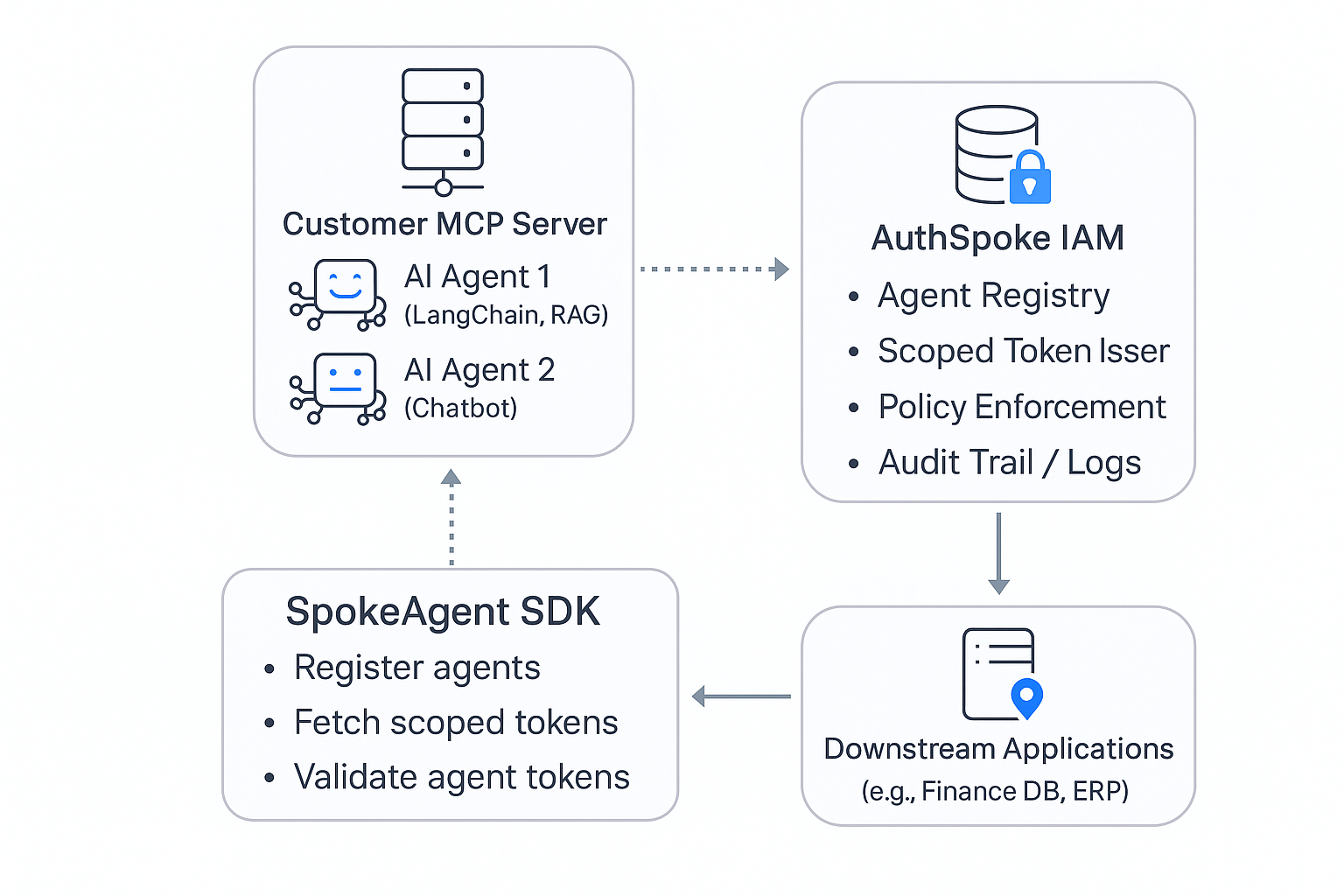
The architecture includes the following:
- MCP Server with standard RBAC / ABAC policy engine
- AuthSpoke Agent IAM as the trust broker
- AgentSpoke SDK embedded in the MCP environment to register, issue, and rotate agent credentials
- AI Agents communicating securely through managed tokens and policy-synced access scopes
Architecture Diagram
4. Agent Lifecycle within MCP
- MCP application triggers agent registration through AgentSpoke SDK.
- AuthSpoke issues agent ID, scoped tokens, and lifecycle attributes.
- Agents interact with MCP services using those scoped tokens, which MCP validates against the AuthSpoke policy store.
- Agents are rotated / revoked periodically as per lifecycle policy (e.g., 30-day expiry, rotate every 7 days).
- MCP logs audit trails of agent access using AuthSpoke events.
5. IAM Flow
The following sequence explains how the MCP communicates with the AgentSpoke SDK:
- MCP authenticates to AuthSpoke with an admin token to manage agents.
- Calls
register_agent with metadata and role mappings.
- Receives a unique
agent_id.
- Requests scoped access tokens for that agent.
- Distributes token to AI agent for secure service-to-service calls.
- Periodically rotates / revokes tokens based on security policy.
6. Code Example
from spokeagent_sdk import SpokeAgentClient, SpokeAgentConfig
# MCP application boot
config = SpokeAgentConfig(
base_url="https://mcp.authspoke.com",
api_key="your_admin_token"
)
client = SpokeAgentClient(config)
# Register agent
agent = client.register_agent(
agent_name="financial-ai-agent",
metadata={"role":"forecasting","env":"prod"}
)
print("Agent registered:", agent)
# Issue scoped token
token = client.get_token(
agent_id=agent["id"],
scopes=["read:forecasts"]
)
print("Agent token:", token)
# MCP can then pass this token to the AI agent
# which calls back the MCP core securely
7. Best Practices
- Use short-lived tokens, rotating them frequently
- Use RBAC/ABAC roles in AuthSpoke to prevent agent privilege escalation
- Validate token claims server-side in MCP services
- Maintain an audit trail of all agent registration and token requests
- Map agent roles to your existing MCP application roles for fine-grained control
8. Lifecycle Protocol Hooks
Integrate MCP lifecycle triggers (e.g. startAgent, stopAgent, rotateAgent) to hook directly into the AgentSpoke SDK. For example, on stopAgent, you can revoke the token:
client.revoke_token(agent_id="financial-ai-agent")
9. Conclusion
By embedding AgentSpoke SDK into an MCP server environment, financial or mission-critical workloads can adopt AI agents with confidence, preserving strict identity and access boundaries. This layered architecture ensures zero-trust and protects sensitive data from unauthorized agent behavior.
