Unlocking the Power of SAML: A Deep Dive into Seamless Single Sign-On
Sagar Paul
Overview
SAML (Security Assertion Markup Language) is an open standard that allows identity providers (IdPs) to pass authorization credentials to service providers (SPs). This mechanism enables Single Sign-On (SSO), enhancing both user convenience and security by eliminating the need for multiple logins across different applications.
What is SAML?
SAML is an XML-based framework for communicating user authentication, entitlement, and attribute information. Its primary purpose is to facilitate the exchange of security information between trusted business partners. SAML enables web-based authentication and authorization scenarios including cross-domain SSO.
The SAML Flow: Step-by-Step
SP-Initiated SAML Flow
SP-Initiated SAML Flow
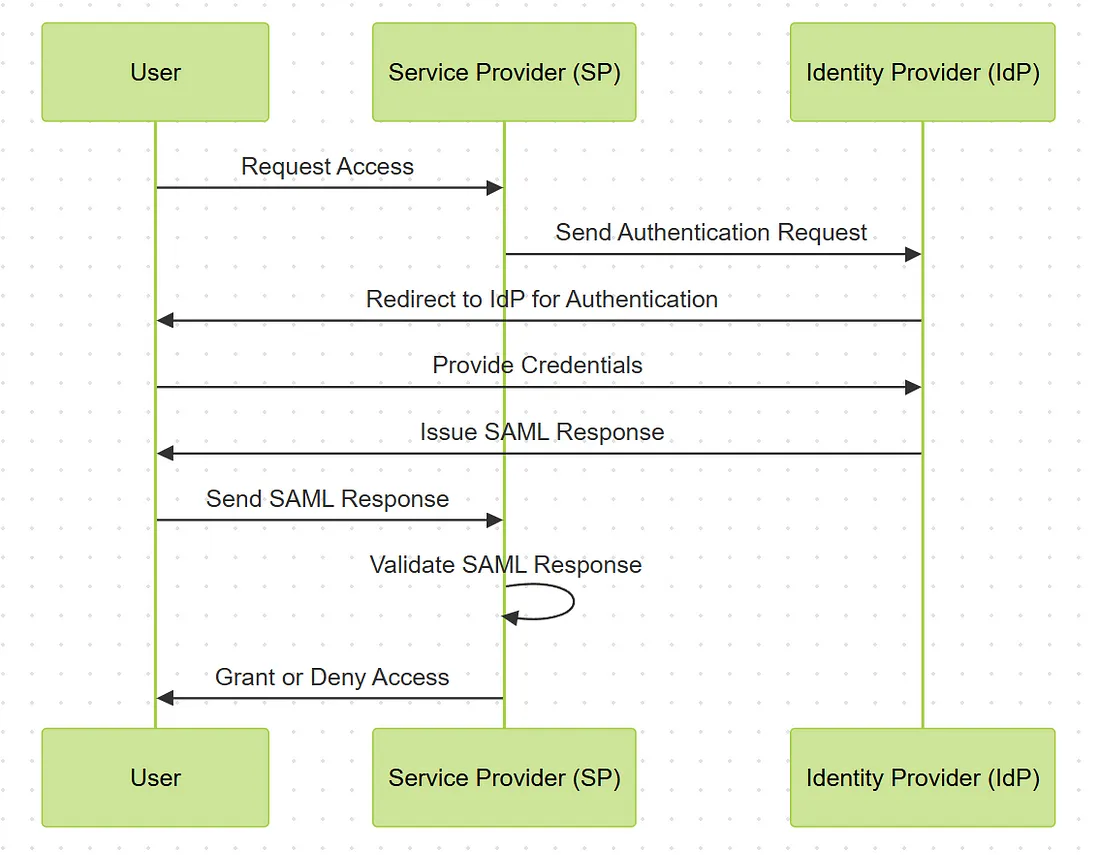
- User Requests Access: The user attempts to access a service provider (SP).
- SP Sends Authentication Request: The SP redirects the user to the identity provider (IdP) for authentication.
- User Authenticates: The user provides credentials to the IdP.
- IdP Issues SAML Response: Upon successful authentication, the IdP generates a SAML response, containing assertions about the user’s identity and attributes.
- User Redirects to SP: The user is redirected back to the SP with the SAML response.
- SP Validates SAML Response: The SP validates the SAML response and grants or denies access based on the assertions provided.
IdP-Initiated SAML Flow
IdP-Initiated SAML Flow
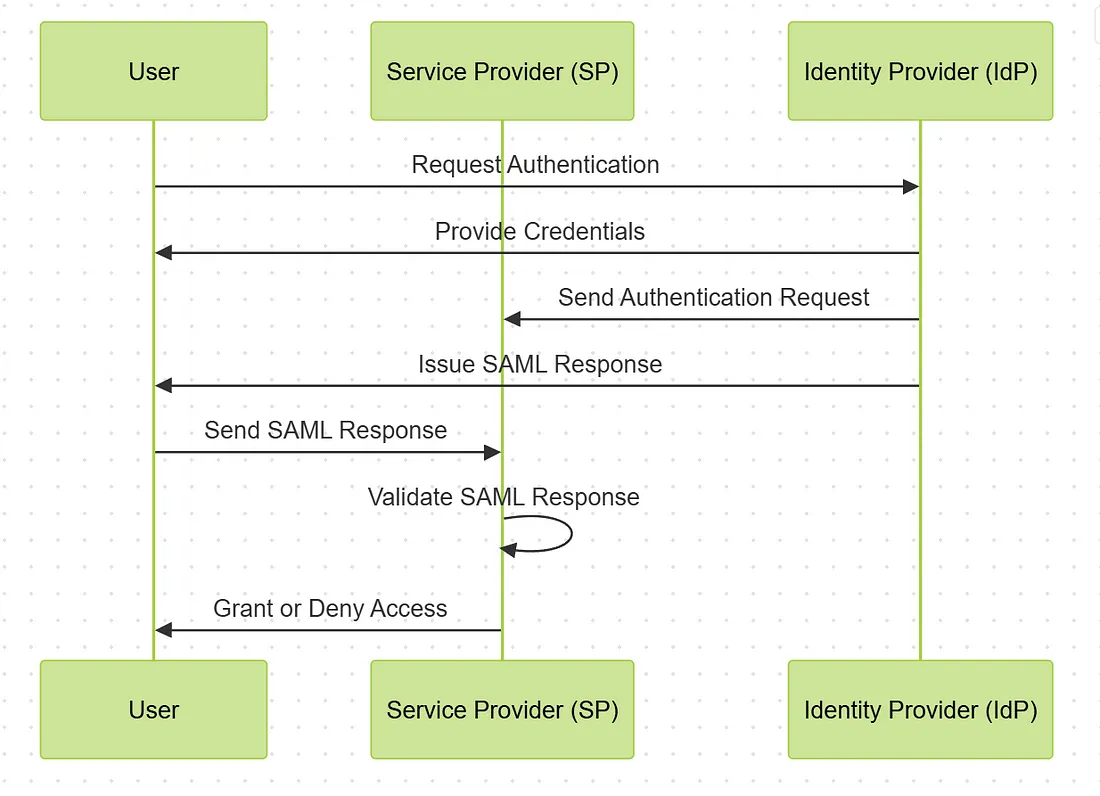
- User Requests Authentication: The user initiates the authentication process at the identity provider (IdP).
- IdP Authenticates User: The user provides credentials to the IdP.
- IdP Sends Authentication Request: Upon successful authentication, the IdP sends an authentication request to the service provider (SP).
- IdP Issues SAML Response: The IdP generates a SAML response, containing assertions about the user’s identity and attributes.
- User Redirects to SP: The user is redirected back to the SP with the SAML response.
- SP Validates SAML Response: The SP validates the SAML response and grants or denies access based on the assertions provided.
Key Attributes of SAML Payload
Assertions: Assertions are statements about the user. There are three types: Authentication, Attribute, and Authorization Decision assertions.
- Issuer: Identifies the authority that generated the SAML assertion.
- Subject: Refers to the user who is being authenticated.
- Conditions: Specifies constraints and restrictions on the assertions, such as time validity.
- Signature: Ensures the integrity and authenticity of the SAML assertion.
AuthnRequest (Authentication Request):
- ID: A unique identifier for the request.
- IssueInstant: The time at which the request was issued.
- Destination: The URL where the request should be sent.
- ProtocolBinding: The SAML binding to be used when returning the response.
- AssertionConsumerServiceURL: The URL to which the response should be sent.
- Issuer: Identifies the entity making the request.
- NameIDPolicy: Specifies constraints on the format of the NameID in the response.
- RequestedAuthnContext: Specifies the desired authentication context (e.g., password, multi-factor).
<samlp:AuthnRequest
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
ID="_af4e2c86b5de9855a"
Version="2.0"
IssueInstant="2025-01-18T14:31:00Z"
Destination="https://idp.example.com/SAML2/SSO/POST"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
AssertionConsumerServiceURL="https://sp.example.com/SAML2/ACS">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://sp.example.com/SAML2</saml:Issuer>
<samlp:NameIDPolicy
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
AllowCreate="true"/>
<samlp:RequestedAuthnContext
Comparison="exact">
<saml:AuthnContextClassRef xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport
</saml:AuthnContextClassRef>
</samlp:RequestedAuthnContext>
</samlp:AuthnRequest>Security Features of SAML
- Encryption: SAML supports encryption of data to ensure privacy and confidentiality during transmission.
- Digital Signatures: Ensures the authenticity and integrity of the assertions by digitally signing the SAML documents.
- Time-Based Conditions: SAML assertions include conditions that specify time validity to mitigate replay attacks.
- Secure Transport: Typically, SAML exchanges occur over HTTPS to protect against eavesdropping and man-in-the-middle attacks.
Differences and Use Cases
SP-Initiated SAML Flow
Difference: The authentication request is initiated by the service provider when a user attempts to access its resources. The SP redirects the user to the IdP for authentication.
Use Cases:
- When the user tries to access a specific application or resource.
- Commonly used in enterprise environments where multiple services are accessed through a single sign-on portal.
IdP-Initiated SAML Flow
Difference: The authentication request is initiated by the identity provider when a user logs in directly to the IdP. The IdP then sends the authentication request to the service provider.
Use Cases:
- When the user logs in through a central identity provider and then gets access to various linked applications.
- Useful in scenarios where users typically start their session from a central authentication portal, such as a company’s intranet or an academic institution’s login system.
🚀 Elevate Your IAM with AuthSpoke
At AuthSpoke, we understand the complexities of modern identity and access management. Our modular, intelligent, API-first IAM platform is designed to simplify SSO and secure your enterprise, allowing your developers to focus on building innovative products.
Discover how AuthSpoke can streamline your identity infrastructure:
Sagar Paul
Founder, AuthSpoke
Identity nerd. DevSecOps advocate. Builder of secure-by-default systems.
 Authspoke
Authspoke